 1200
627
1200
627
Written by
Simon Jackson
Simon bring more than 20 years of experience in cloud architecture, networking, infrastructure design. He holds a BSC in Physics from Lancaster University and a postgraduate Master's programme in Cloud Computing from Caltech CMTE as well as holds the globally respected CISSP certification. His academic and professional background spans Microsoft Azure, Amazon Web Services (AWS) and Google Cloud Platform (GCP), underpinned by a strong focus on AI, DevOps and Automation.
If you’ve ever stood in line at airport security, you’ll know the drill: remove your coat, take off your shoes, place your liquids in a clear bag, place your laptop out, and wait. It’s the worst part of the airport experience… but one missed step and the consequences ripple far beyond your boarding pass.
Your supply chain is no different. It’s not just the internal systems you need to lock down. Every partner, every provider, every plug‑in and third‑party link. One weak-link in the connection, and you’ve let the wrong person through the metal detector.
The Rising Risk in Supply Chains
Cybercriminals aren’t always going after the big targets directly any more. They’re climbing in via an open window, the SME suppliers, the service providers, the sub‑contractors with weaker defences.
As seen in the SolarWinds and SonicWALL hacks, attackers compromised a trusted vendor, then used that relationship to infiltrate much larger organisations. And it’s not just IT companies, in the last four years some very public names have all been attacked
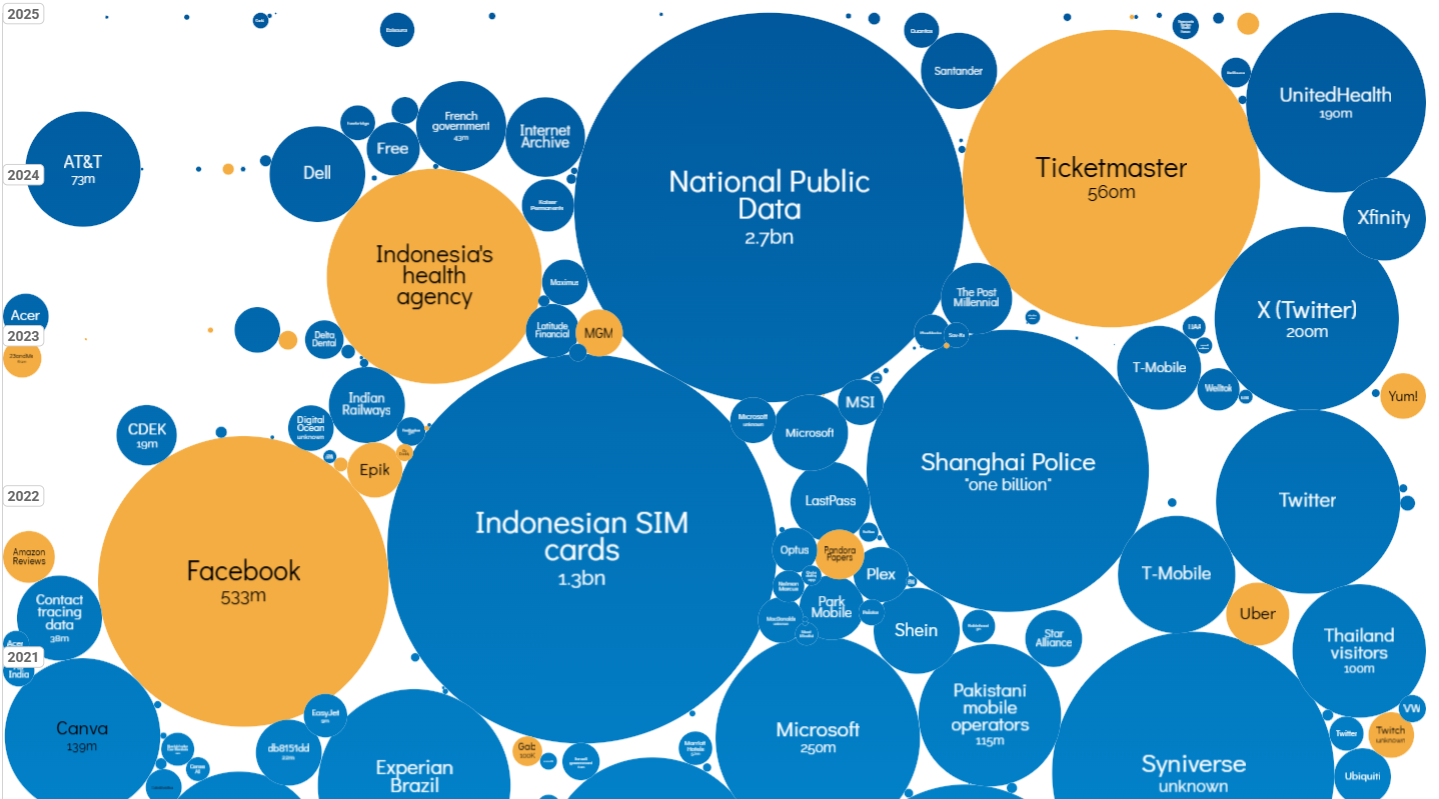
Source: World’s Biggest Data Breaches & Hacks — Information is Beautiful
This is non-exhaustive list of notable, well‑reported, incidents:
– Jaguar Land Rover – A production and supply‑chain disruption reported after a cyber incident in mid/late‑2025 (reported across press summaries of 2025 incidents). Raconteur
– Marks & Spencer (M&S) – In April 2025 M&S suffered a major cyber incident that is reported to involve a third‑party service provider access / supply‑chain vector – insofar as publicly reported. According to commentary, this is characterised as a “supply chain attack.” TrustWave
– Peter Green Chilled – A chilled‑food distributor supplying big UK supermarkets including Tesco, Sainsbury’s, Aldi, was hit by a ransomware attack in May 2025. The disruption affected its ability to process orders to its retailer customers, a clear supply‑chain attack vector. Wired
If you think “we’re too small to be targeted”, remember: you may not be the target, but you could be the route into someone else.
Why Regulation is Turning the Screw
UK organisations can no longer ignore the regulatory pressure to secure their supply chains. While the Data Protection and Digital Information Bill (DPDI) ultimately lapsed in 2024 following the general election, its core intent hasn’t disappeared. In its place, the Data Use and Access Act 2025 (DUA) has introduced updated obligations around data processing, third-party access, and accountability across the supply chain.
Key pressures now include:
- Tighter third-party oversight – Businesses are increasingly accountable for how partners and suppliers handle data. “It wasn’t our breach” is no longer a viable excuse.
- Mandatory breach notification and auditability – You’re expected to demonstrate proactive governance over your vendors, including contracts, access controls, and response readiness.
- Increased ICO scrutiny – Regulatory bodies are now scrutinising not only if data was breached, but how well you knew and managed the risk in advance.
Legislators are closing the gap between owning risk and sharing risk – especially when sensitive data crosses into your supply chain. If your vendors can access personal data, credentials, or production systems, then their vulnerabilities become your liabilities.
The bar is rising… it’s not just about GDPR compliance anymore. It’s about demonstrating that your business has the controls, contracts, and culture in place to prevent your partners from becoming your weakest link.
Going Beyond the Basics: Cyber Essentials as the Entry Standard
Alltime Technologies affiliate with National Cyber Security Centre (NCSC) as an Certification Body for the Cyber Essentials programme. NCSC designated IASME as the Cyber Essentials Scheme Operator. You can find us on the IASME Network Directory.
Think of Cyber Essentials like the airport scanner for your supply chain: it won’t eliminate all risks, but it helps screen out the most common attack vectors. These are weak firewalls, poor configuration, inadequate access control, missing patches, and unchecked malware.
By asking your suppliers to hold this baseline (or a higher standard), you raise the minimum bar — and reduce the chances you’re the one who forgot to remove their belt.
A Deeper Lens: The Cyber Posture Assessment
If Cyber Essentials is raising the correct controls; Cyber Essentials Plus in the scanner that proves the controls are in-place. Then we can look at our Cyber Posture; performing a Cyber Posture Assessment as a full security walkthrough – like going through a mock‑up emergency drill before the gate is even open. It answers some key questions:
- Where are your current cyber weaknesses?
- How do your suppliers interact with your systems and data?
- What needs improvement, and where should you prioritise?
Key steps for a Cyber Posture Assessment:
– Identify your critical systems: where sensitive data lives or flows.
– Assess access controls: are the right people accessing the right data?
Are third parties active in this?
– Test defences: simulate attacks or review controls in the loop of third‑party interfaces.
– Review supplier connections: how do they access or store your data, and how are they secured?
– Prioritise remediation: fix the highest risk areas first, then build continuous monitoring.
Best Practice Principles for Supply Chain Security
- Treat suppliers as if they were internal systems. Validate, don’t assume.
- Set clear expectations for your supply‑chain partners, demand Cyber Essentials certifications or higher, require MFA, require incident readiness.
- Include third‑parties in your incident‑response plans, suppliers should be part of your scenario planning.
- Continuously assess risks; supply chains change, access changes, systems change. Annual checks are only the start.
Final Thoughts
Your supply chain is only as strong as its weakest link. If one small provider, one single mis‑configured service, or one overlooked contract medium handles your data, you could be the entry point. It’s not just about hygiene; it’s about operational resilience and reputational risk.
Trust must be earned and continually validated. Without clear oversight, even your most reliable partner can introduce unexpected risk. Like airport security, you don’t need the drama of thousands of steps; just the right structure, accountability and mindset.
Take control. Reduce exposure. And secure your supply chain with confidence.
And talk to us if you have any questions, we are here to help.
